How ransomware works (with controls)
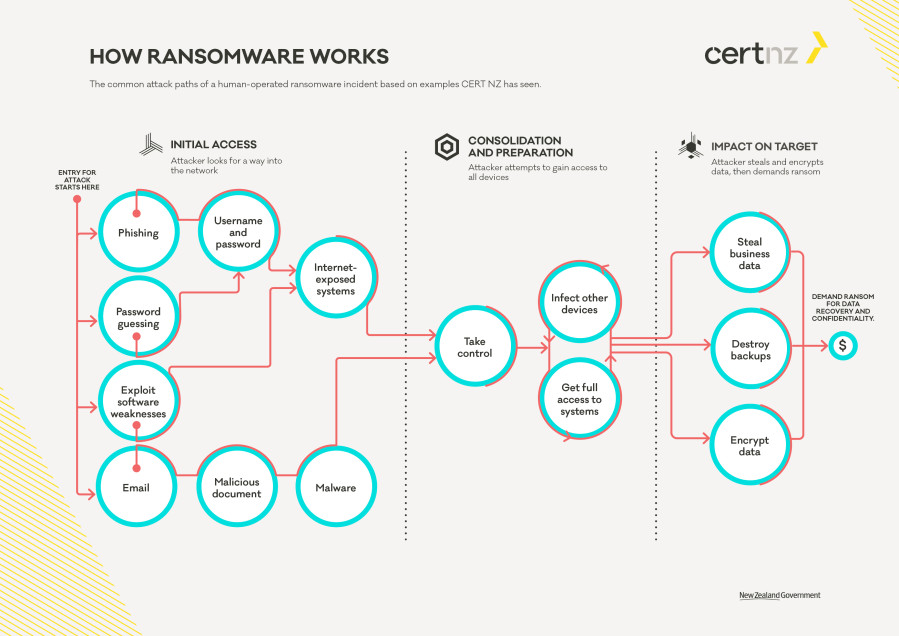
This diagram shows how ransomware attacks happen and is split into three phases showing the entry points of an attack and following the pathway across until the point where a ransom can be demanded.
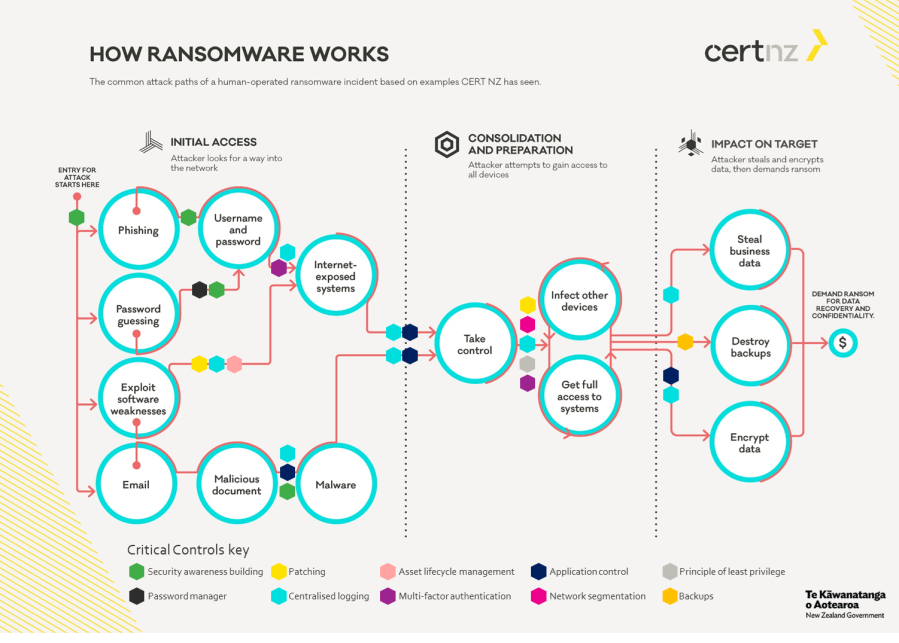
A defence-in-depth application of CERT NZ’s Critical Controls provides a strong defensive net to detect, prevent and respond to any potential ransomware attack before your data is encrypted.
The diagram references these Controls at the relevant intervention point.
The first phase shows how the attacker looks for ways into the network.
• Security awareness building.
• Patching.
• Multi-factor authentication.
• Password manager.
• Centralised logging.
• Application control.
The second phase shows how the attacker will look to move from the initial computer they compromised and gain administrative access to all the computers and devices in your business.
The Critical Controls referenced are:
• Centralised logging.
• Patching.
• Application control.
• Network segmentation.
• Principle of least privilege.
The third phase shows when the attacker has gained access to the different systems in your business and is now ready to carry out the most damaging part of the attack.
The third phase shows the impact on target which include data exfiltration, destroy back-ups and encrypt data.
The Critical Controls referenced are:
• Backups
• Centralised logging.
• Application control.
Each of the relevant controls is marked by a coloured hexagon:
• Rose for asset lifecycle management.
• Yellow for patching.
• Purple for multi-factor authentication.
• Green for security awareness building.
• Navy for application control.
• Light blue for centralised logging.
• Black for password manager.
• Grey for principle of least privilege
• Pink for network segmentation.
• Gold for backups.