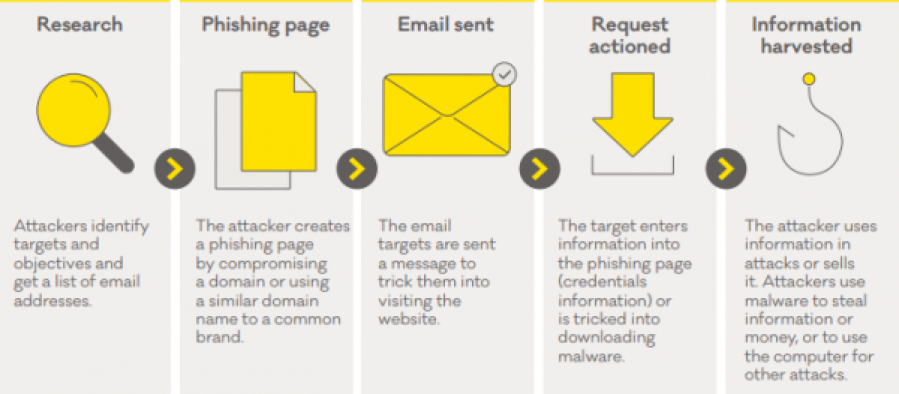
What it is
Phishing is a type of email scam. A phishing email will ask you to either click a link and enter personal information, or open an attachment in the email. The scammer might make it look like the email comes from your business.
One of the challenges with phishing is that it exploits people’s everyday behaviour. Businesses often send emails to customers asking them to:
- click on links to the business’s website
- log into their account when they get there.
Phishing scams mimic this behaviour to:
- trick customers into giving up their information or account login details, or
- install
software – like ransomware – on peoples' computers.
wanting to cause harm
Spear phishing and whaling
Spear phishing and whaling scams are more targeted types of
when a scammer pretends to be someone else, like a bank or NZ Post, usually via email, trying to get your personal information or even money.
In a spear phishing attack, people within a company receive an email asking them to provide the sender with confidential company information. The emails will look like they’ve come from a particular department or person in the company.
Whaling specifically targets the management or executives in a company — the ‘big fish’. These are usually the people who have the most authority and the most access to sensitive business information.