[Audio/Visual]: As the screen opens, quiet music plays in the background. The music plays throughout the video. The screen opens displaying a person with her left side to camera, standing in front of bunches of bright flowers. They are watering them with their right hand. The background is blurred but there is a working station/desk and more flowers.
Narration starts immediately, as it does, the person moves about watering the bunches of flowers.
[Audio/Narration]: ‘Meet Marama, she’s a florist.’
[Visual]: Frame changes to a new scene with a person sitting on a dark green couch. They are looking down at a laptop in front of them which sits on a low coffee table. The couch has yellow accents with cushions and a throw rug. The room they are sitting in has grey carpet and the wall has colourful artwork. The coffee table has hexagon coasters sitting next to the laptop.
The person while looking at their laptop is waving their hands up in frustration and goes back to typing. They then pick up a cell phone, and the frame zooms in closer to a waist shot.
[Audio/Narration]: “She gets a call from one of her regular customers, Peter.’
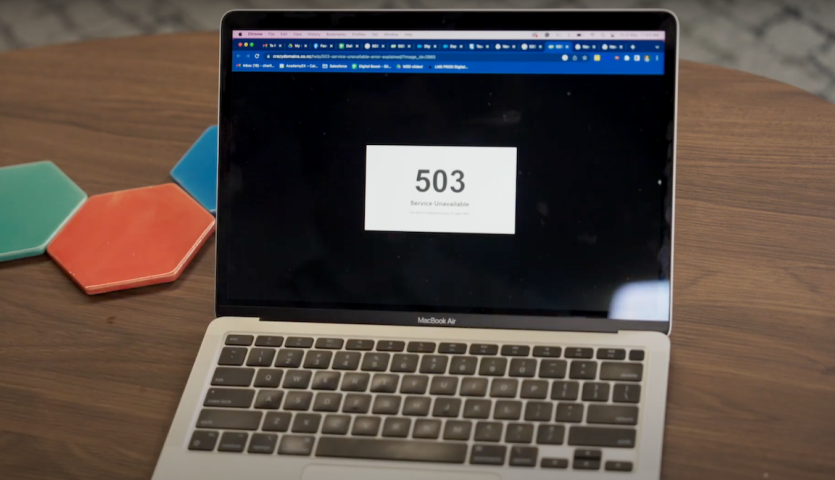
‘Peter is trying to order flowers from Marama’s website, but the website won’t load, and is showing an error message - 503 Service Unavailable.”
[Visual]: As the call takes place, the frames swap back to the florist who is putting together a bunch of flowers at the service desk. The bunches she was watering in the opening scene are in the background, and more shelving with glass jars can also been seen. The florist is holding a phone in her left hand. As the call is taking place, the florist has a concerned / confused look on their face.
The scene changes back to a view of the caller’s laptop. Their hand is in frame, pushing buttons on the keyboard. The laptop screen has a 503 service unavailable error message. The scene pops back to the florist, and then back to the caller to illustrate the conversation on the phone. The last shot of the florist has her nodding her head as she is being told about what the issue might be.
[Audio/Narration]: “Marama is confused, and Peter suggests she might be being DDoSed, and working in cyber security, tells her more about it.”
[Visual]: A new scene with a person looking straight to camera appears. The person has the same authority and sounds the same as that who is narrating. They are standing at waist height in a teal long sleaved top with frilly details. They have a mic and red nail polish. The backdrop to this scene is a room with tables and chairs and green painted walls. There are inside plants scatter around and on the tables. As they are explaining what DDoS stands for, the screen displays words in white colouring “DDoS Distributed Denial of Service attack” to the top right-hand side of the screen.
[Audio]: “A DDoS stands for distributed denial-of-service attack, aimed at stopping online websites and tools from working, by overloading them.
Networks can only process a certain number of requests at once, so the attack works by flooding a website with false requests, blocking any genuine requests from getting through.”
[Visual]: The screen cuts to a bird’s eye view of a busy motorway showing overhead bridges and offramps. Lanes are blocked with a lot of cars going one way and freely running on the other. The screen pans out / camera gets higher showing more and more of the motorway as the audio continues.
[Audio/Narration]: “Think of it like intentionally causing traffic jams on a motorway and shutting down a city, by adding thousands of cars to the roads.”
[Visual]: Scene cuts back to the narrator talking direct to screen.
[Audio] “When this happens, your customers may not be able to access your website, order goods or services from you, pay you, or even contact you.
You can spot a DDoS attack in a few ways, like being unable to load your website…
[Visual]: narration continues, the scene pops back to the person on the couch looking frustrated and back to the laptop 503 error message view.
[Audio/Narration] “…your website being so slow that it’s unusable, your internet constantly disconnecting or timing-out, or 503 Service Unavailable Errors.”
[Visual]: Florist is back on screen
“So what do I do?” Marama asks Peter.
[Visual]: New shot showing screen mirroring of CERT NZ’s reporting tool. “Report an issue” is at the top of the page and the mouse moves through the reporting tool showing the steps required to take to report a DDoS incident. This includes drop down options to select the situation that best describes the issue the reporter is having. This example selects the following – (chosen options in italics):
I’d like to report something that happened [to me] [in the last week.]
I’ve had an issue with [a website.] I [think something is wrong with my website] because [there is an issue or an error on it.] [I don’t know what to do]. [The issue hasn’t been resolved.]
Along the bottom of the screen, a url link appears showing a direct link to the online reporting tool: cert.govt.nz/individuals/report-an-issue/
Once all options are selected, the following text appears at the bottom: It sounds like someone has gained access to your website without your knowledge.
[Audio/Narration] “Report the incident with CERT NZ, through their website. Provide everything you know, as well as your contact details, so CERT NZ can provide confidential advice to help you through the attack.
[Visual]: New scene of florist sitting at a desk with desktop computer in front of her. She has her left hand up to her mouth and her right hand is placed on the mouse. The scene flicks to a closer head shot of the florist, with the camera panning left to right from behind her screen. The florist’s eyes indicates they’re looking at the form filling in the drop down selections.
[Audio/Narration] “and assist you in talking to your managed service provider or website host for more help.
[Visual]: The last scene brings back the narrator looking and talking direct to screen scene. A phone number 0800 CERT NZ slides on to the screen in the bottom right corner.
[Audio] ‘Head to the report an issue page on CERT NZ’s website to report or you can also call CERT NZ on 0800 CERT NZ.
[Visual]: Closing slide appears with slightly louder backing track. The screen is blue with the CERT NZ logo at the top. Underneath the logo, there is white text ‘For more cyber security advice, go to cert.govt.nz.’ The Digital Boost logo is in the bottom left corner and the New Zealand Government logo is in the bottom right corner.