What it is
a card used in mobile phones (and other mobile devices) used to identify the device and connect to networks.
How it works
First, an attacker will try to get hold of private information that they can use to impersonate you, like your date of birth and address. For example, they could find details about you from:
- your social media accounts
- private information that's been leaked
- information that's publicly available online.
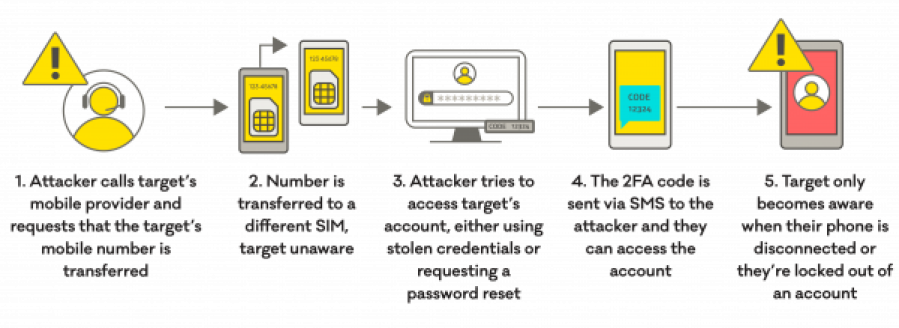
The attacker will then contact your mobile phone company pretending to be you, and if they've found out the right type of information, they'll use it to answer any security questions the provider asks. Then they'll ask to have your mobile phone number transferred to their SIM card. Once they've done that, they can access your text messages and voicemail, all without you knowing.
This kind of attack brings a lot of risk with it.
If an attacker gets access to your text messages and voicemail, it would give them access to a lot of personal information they could use to perform sensitive tasks. For example, if they can find out or guess the password for any of your other accounts, like your email or bank account, they could:
- change your passwords, denying you access to your accounts
- authorise financial transactions from your bank accounts.
And, if you're using text based
a security setting that needs an extra piece of information, such as a text code or fingerprint, to log in to your account.